Key Insights: Decoding RBI instructions on Card Payments Security

At first glance, the basics of complying to RBI guidelines seem quite straight forward. However, the advancements in the forms and patterns of cyberattacks has made the RBI instructions on card payments security more dense and complex. For instance, RBI states that regulated entities shall follow payment card standards such as PCI PIN and P2PE.
We conducted a panel discussion with some of the brightest minds in cybersecurity and compliance to decode RBI instructions on card payments security. Moderated by Dharshan Shanthamurthy, CEO of SISA, the following members joined the discussion as esteemed panellists:
- Sameer Ratolikar, Executive Vice President & CISO, HDFC Bank
- Vijayakumar Chandrasekaran, Head of ICS, India, Standard Chartered Bank
- Nitin Bhatnagar, Associate Director – India, PCI Security Standards Council
- Kaushik Pandey, Head – Compliance & Testing, SISA
The responses of our panel discussion attendees helped us understand that although companies are planning to comply to the RBI guidelines, the preparadness is lacking proper understanding of the security controls and important regulatory requirements. In such a climate, and with organizations attempting to comply to multiple payment regulatory requirements, CISOs and risk & compliance leaders should put the right controls in place to prioritize PCI PIN & P2PE standards.
Read on to take a deeper dive into the frontline trends in the subjects around RBI guidelines and PCI PIN, P2PE regulations. Also, the followings insights are responses to some of the frequently asked questions on our panel discussion. The responses to these questions can help compliance seekers put the right security investments, processes and risk management strategy on a firm footing to help achieve compliance on all fronts including RBI and PCI guidelines for payments card security.
1. Is PCI PIN controls applicable in banks as per RBI digital security framework?
SISA response:
Applicability of PCI PIN standard (as per Payment Brands) covers the following domain:
- PIN acquiring payment processing – POS
- PIN acquiring payment processing – ATM
- Remote key distribution using asymmetric keys
- Certification and registration authority operations
- Key Injection facilities
In case the Bank is managing any of the above domains, PCI PIN is applicable on them and they are required to attain PCI PIN compliance. If the Bank has outsourced these activities to any 3rd party vendor, then the Bank needs to ensure that the vendor is PCI PIN certified/compliant.
However, RBI Circular is not specific about Acquiring and/or Issuing Scope, so as a best practice and to adhere compliance as per RBI Master Circular, we request the Banking Institutions to cover both i.e. Acquiring and Issuing.
2. Please throw some light on PCI PTS, PCI HSM, PCI P2PE, and what banks are supposed to do. How the industry is implementing?
SISA response:
PCI PTS standards apply to POI/POS devices, Encryption PIN Pads, POS devices, HSMs, Unattended payment terminals etc. It is the responsibility of the hardware vendor to get these devices PCI PTS certified. Banks need to ensure that the devices they are deploying across merchant locations are PCI-PTS Certified.
PCI PTS HSM standard covers physical, logical and device security requirements for securing the HSM devices. Banks are required to ensure that HSM deployed in the environment are PCI PTS HSM certified, generally HSM Vendors are required to support all the secure functionalities as per the standard and Banks can evaluate their HSMs for secure configuration review, please refer to the below listing for further updates on POS/HSMs which are PCI PTS Compliant – https://www.pcisecuritystandards.org/assessors_and_solutions/pin_transaction_devices?agree=true
PCI P2PE standard covers encryption, decryption and key management requirements for point-to-point encryption solutions (Point of Sale à Payment Switch). Banks need to ensure that the assets involved in point-point solutions are PCI P2PE compliant. If the Bank is managing these assets then the Bank needs to attain PCI P2PE compliance. In case these activities are outsourced to any 3rd party vendor, then the Bank needs to ensure that the vendor is PCI P2PE compliant. Please refer to the below listing for further updates on PCI P2PE Compliance Solutions – https://www.pcisecuritystandards.org/assessors_and_solutions/point_to_point_encryption_solutions
3. How PCI P2PE applicability can be defined?
SISA response:
PCI P2PE solutions must include all of the following:
- Secure encryption of payment card data at the point-of-interaction (POI)
- P2PE-validated application(s) at the point-of-interaction
- Secure management of encryption and decryption devices
- Management of the decryption environment and all decrypted account data (Payment Switch)
- Use of secure encryption methodologies and cryptographic key operations, including key generation, distribution, loading/injection, administration and usage
There are various case studies available on the PCI SSC website that help clarify PCI-P2PE Solution deployments at – https://www.pcisecuritystandards.org/document_library –> P2PE Section from the Dropdown.
4. Now the customers are moving into cloud adaptive – what is your view about moving PCI environment to any cloud technologies (AWS, GCP, or Azure, etc.) and if you have any reference of controls and any use cases to share with us. Is it safe to move PCI environment to cloud?
SISA response:
It is safe to migrate the PCI environment to the cloud, many organizations globally have realized the benefits of digital transformation offered by cloud computing. Most of the well-known cloud platforms like AWS, Azure, GCP etc. are PCI DSS certified and offer multiple certified solutions to reduce the compliance overheads of the organizations. However, it is important to note that the security of the PCI environment on the cloud brings a few challenges which need to be managed keeping the cloud security responsibility matrix in mind. Kindly refer to PCI SSC cloud computing guidelines for more details. (https://www.pcisecuritystandards.org/pdfs/PCI_SSC_Cloud_Guidelines_v3.pdf)
However, please note that none of the cloud environments as of date are PCI P2PE or PCI PIN Compliant/Certified, so banks seeking these compliances will be required to go for a Hybrid approach where system components under P2PE or PIN scope will be required to be hosted on-premise or physical data center.
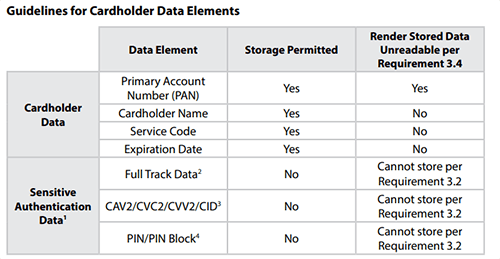
5. Is the absence of storing credit card expiry dates in our systems, we are facing a challenge in notifying the customer about the forthcoming expiry date for Credit card standing instructions, since we are not in the custody of the information. Hence, customers are facing service issues from the Life Insurance industry, as insurers are not proactively intimating about the expiry of the card. Is there any solution from panellists on this?
SISA response:
PCI DSS v3.2.1 allows storage of expiry dates as part of account data storage requirements and is not required to be rendered unreadable at the time of storage. Please refer the storage requirements as highlighted in PCI DSS standard:
6. What is the present status of the PCI standards mentioned in the circular? Is it already released or proposed to be made effective? If so, what will be the effective date?
SISA response:
Please find the present status of PCI standards (highlighted in RBI DPSC):
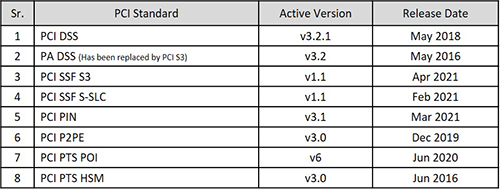
Kindly refer to PCI SSC document library for latest standards and further updates – (https://www.pcisecuritystandards.org/document_library)
These FAQs should serve as a reference and strategic complement to the overall preparedness for RBI guidelines and PCI PIN, P2PE regulatory standards with relevant decision support based on the responses to the panel discussion hosted by SISA. The insights aim to inform cybersecurity leaders, CISOs, risk and compliance executives about emerging regulatory standards in the payments security space, to help them anticipate key compliance movements for the remainder of the 2021 calendar year.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global




 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube






