SISA's Playbook for Surviving Ransomware.
Reduce impact, guide recovery, and restore operations with a structured Ransomware Response Plan built for resilience.
When do Organizations need Ransomware Incident Response
Organizations need to act on Incident Response when they see any of the following:
Files encrypted or renamed, ransom notes, or suspicious admin activity
Lateral movement, privilege escalation, or disabled security controls
Exfiltration alerts, unusual outbound traffic, or data posted on leak sites
Credential dumps, VPN anomalies, or MFA fatigue attacks
Ransom communications or extortion threats
How SISA Sappers Detects and Accelerates Ransomware Recovery
SISA's Ransomware Incident Response helps you contain the attack, verify what was impacted, and get your business back online safely.
SISA Sappers bring deep DFIR expertise in payments and banking, using a structured,
evidence-preserving workflow to contain fast while running clean-room recovery in parallel. Organizations get swift restoration, a clear RCA, and regulatory aligned documentation so your teams get back to business with confidence.
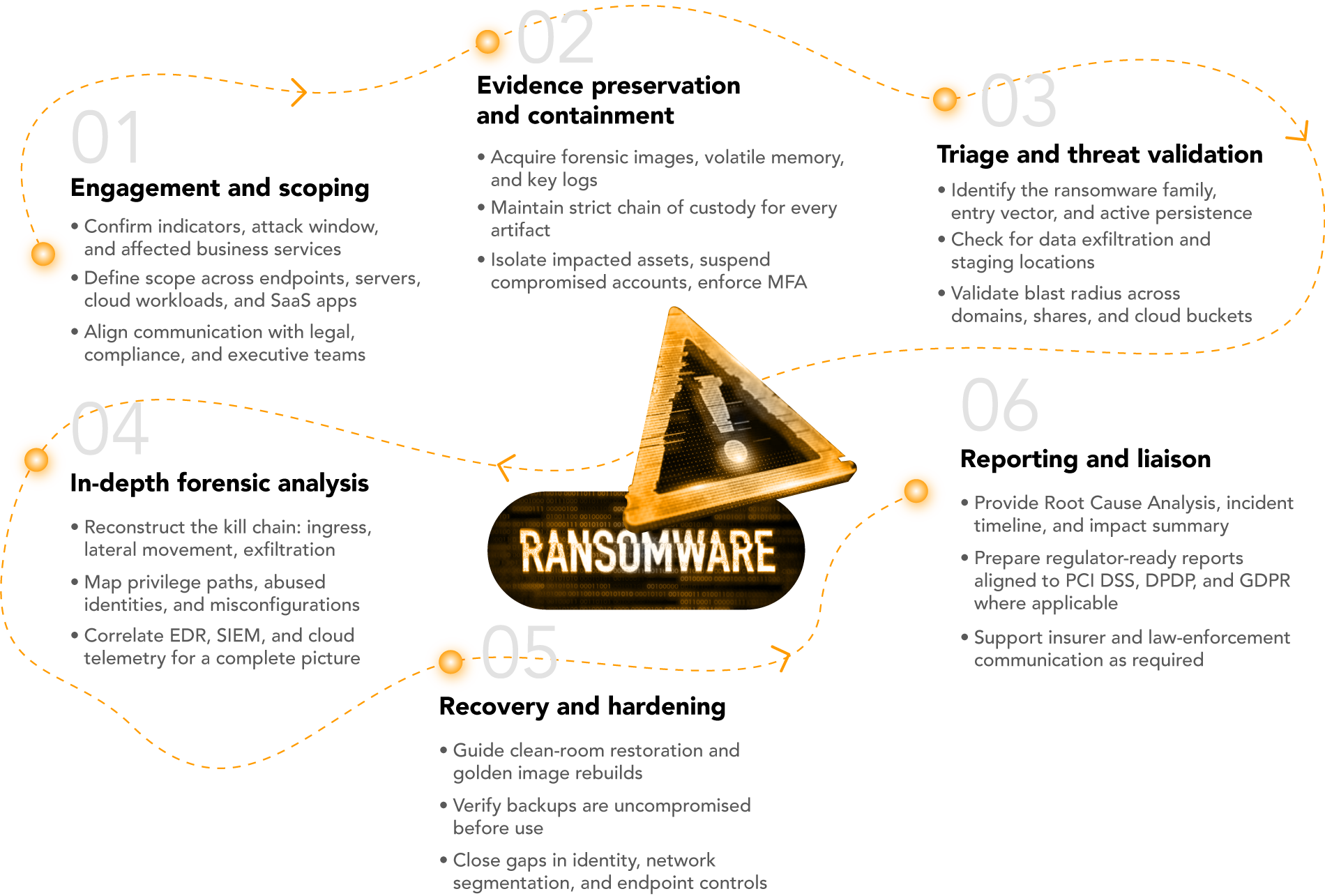
Key Deliverables
Incident Response Report
Scope, timeline, impact, and business risk`
Root Cause Analysis
Entry vectors, exploited weaknesses, and fix list
Evidence Pack
Forensically preserved images and logs
Data Exposure Assessment
What was accessed, exfiltrated, or at risk
Recovery Playbook
Stepwise restoration and verification checks
Hardening Plan
Identity, endpoint, network, and cloud guardrails
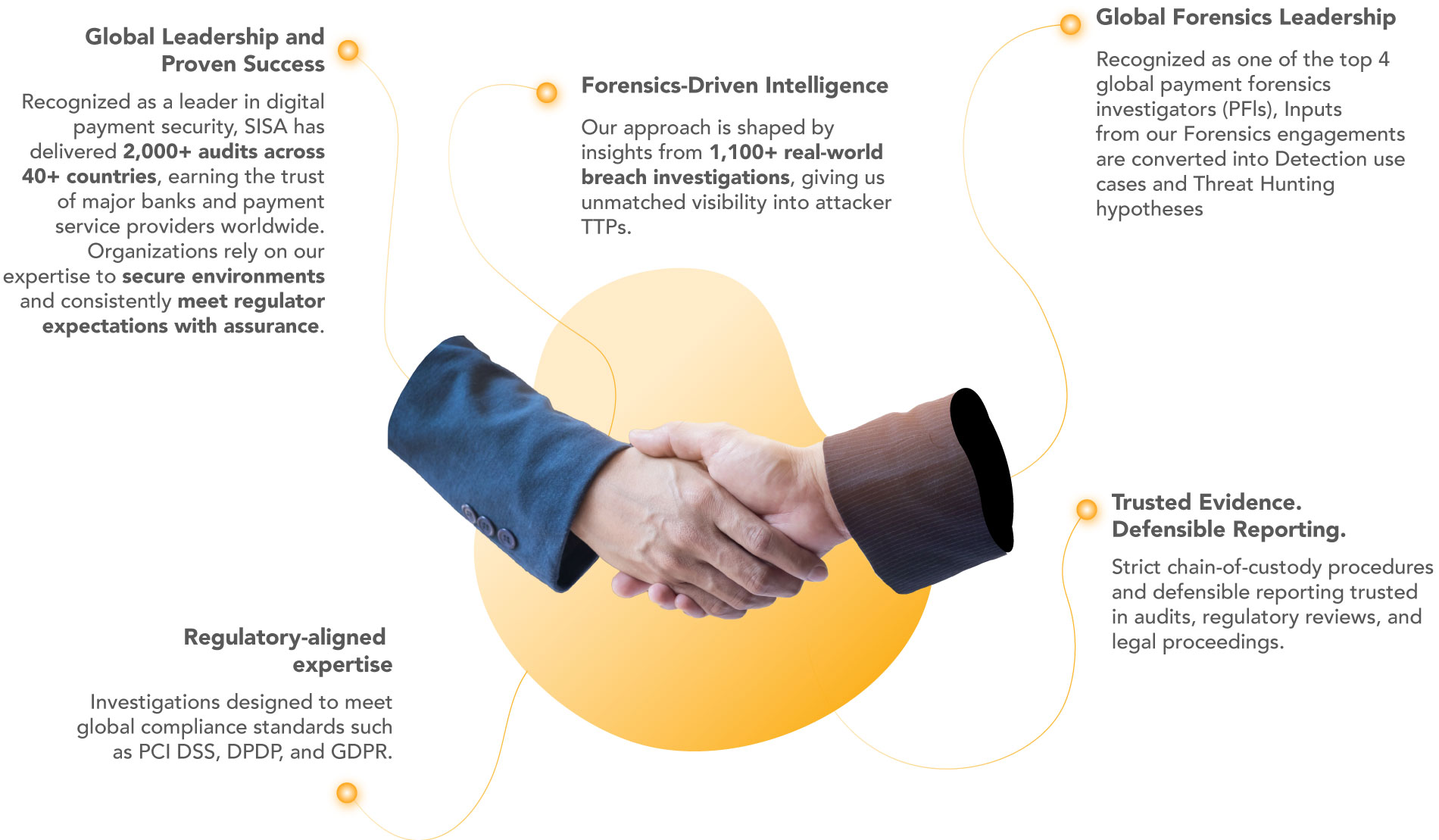
Why Partner with SISA
Suspect a ransomware incident?
Act fast. SISA SAPPERS bring world-class forensics expertise to contain threats, preserve evidence, and safeguard regulatory trust.


 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube






