Breach and Attack Simulation (BAS)
Breach and attack simulation to test your defenses before real attackers do
SISA’s breach and attack simulation (BAS) service is designed to rigorously test and validate the effectiveness of your organization’s detection and protection mechanisms. Through simulated, harmless attack scenarios – based on real-world tactics – we help you assess the maturity of your cybersecurity posture, identify blind spots, and strengthen your ability to respond.
The ultimate goal? To deliver a detailed maturity assessment of your current defences and provide actionable recommendations to elevate your cyber resilience. What SISA BAS helps you achieve:
- Evidence-based validation of your existing security tools like EDR, SIEM, and firewalls
- Identification of gaps in detection and response workflows
- Improved compliance readiness for PCI DSS, ISO, SEBI, and more
- Stronger SOC visibility with expanded use case coverage
- Threat simulations against a wide range of adversarial tactics, including ransomware attacks, aligned with the MITRE ATT&CK framework.
Improve detection, minimize risk, and strengthen resilience using SISA’s 3-Stage BAS methodology
Our Breach and Attack Simulation service is a structured, consultative approach designed to validate security effectiveness across your environment. Grounded in real-world tactics and executed with surgical precision, SISA’s BAS framework includes:
01 Internal threat simulation – exposing risks behind the firewall
We simulate adversarial behaviour within your internal network to test security controls on systems not exposed to the internet. These controlled actions are designed to mimic common attacker behaviours and include:
We simulate adversarial behaviour within your internal network to test security controls on systems not exposed to the internet. These controlled actions are designed to mimic common attacker behaviours and include:
Process invocation and command execution (e.g., PsExec, WMI)
Registry modifications and privilege escalation attempts
User enumeration to assess credential exposure
Deployment via a custom batch file with pre-configured, safe command sets
02 External Threat Simulation – Testing Your Perimeter Defences
We target your public-facing infrastructure with safe, controlled tests to evaluate exposure and misconfigurations from an outsider’s perspective. Activities include:
We target your public-facing infrastructure with safe, controlled tests to evaluate exposure and misconfigurations from an outsider’s perspective. Activities include:
Reconnaissance using tools like Nmap
Simulated attacks via custom web-based scripts targeting known CVEs, misconfigured assets, or weak authentication controls
Testing detection capabilities without disrupting production environments
03 Environment-Ready Execution – Safe, Pre-Qualified Deployment
Every simulation is preceded by careful planning to ensure operational safety and meaningful results. We work with your team to:
Every simulation is preceded by careful planning to ensure operational safety and meaningful results. We work with your team to:
Identify a host machine that is already feeding logs into your SIEM
Confirm availability of target systems (Windows, Linux)
Set up necessary admin access and custom configurations
Validate security telemetry across your entire environment
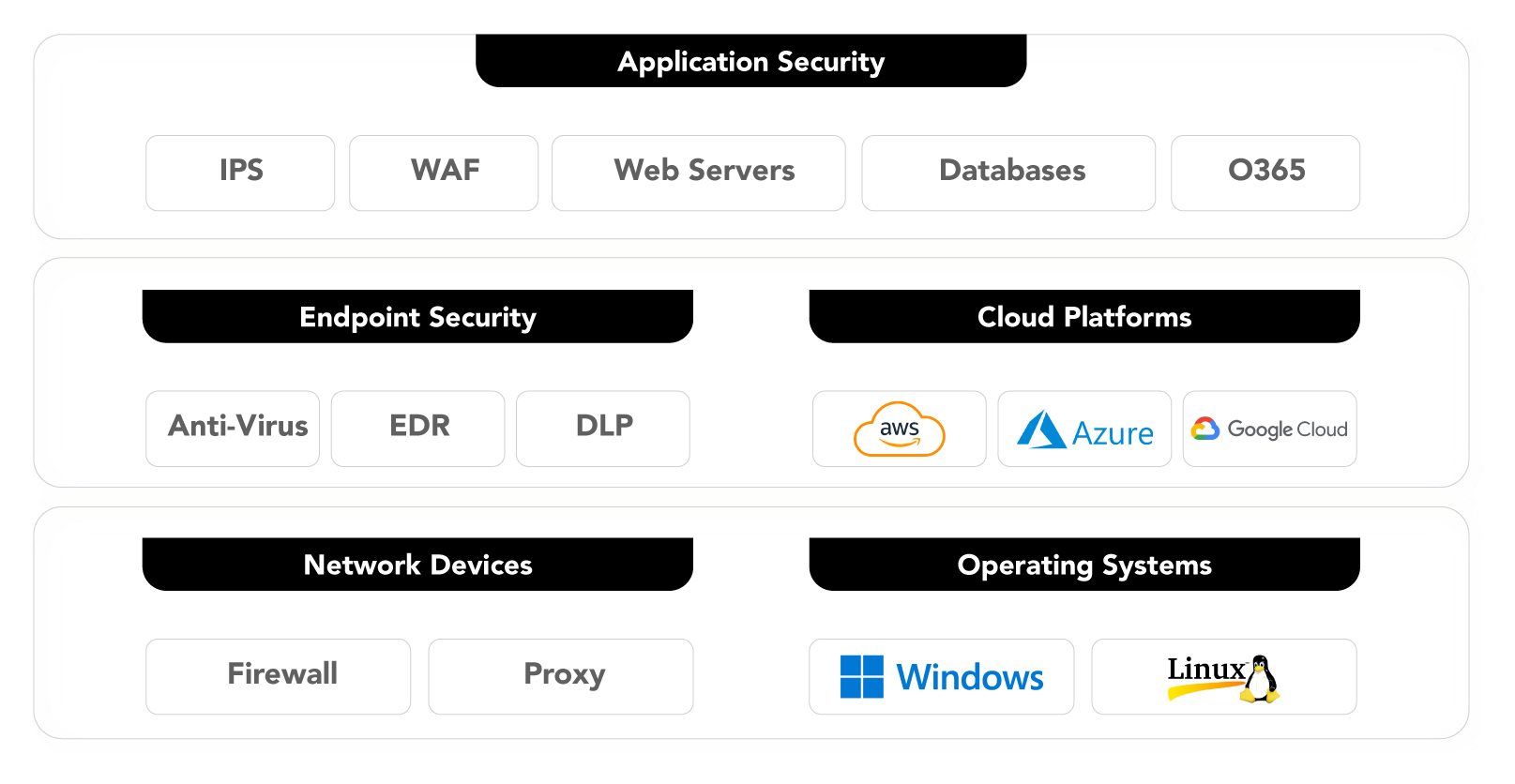
Each simulation is designed not just to mimic adversary behavior but to verify that your detection systems are working as intended. By observing how your tools capture and respond to simulated threats, we help you ensure telemetry is accurate, complete, and actionable. Our BAS exercises validate log collection, alerting, and visibility across:
Get started with breach simulation now!
From simulation to action: Turning insights into security outcomes
SISA’s BAS engagement doesn’t end with simulation, it delivers clarity, direction, and measurable next steps. Once the simulation activities are complete and logs are analysed, you receive a comprehensive report and prioritized roadmap to improve your detection strategy and close critical gaps across people, process, and technology. This includes:
01 Tactic-to-Outcome Mapping
Success/failure ratio of simulations, aligned with MITRE ATT&CK tactics.
02 Technique-Level Analysis
03 Security Control Evaluation
04 Gap Identification
05 SOC Performance Assessment (if applicable)
06 Use Case Coverage Review
07 Mandatory Use Case Recommendations
08 Optimization Opportunities
Why choose SISA for breach & attack simulation (BAS)?
Custom attack scenarios
Tailored simulations aligned to your environment and mapped to MITRE tactics - not generic tests.
Intel-driven use cases
Use cases built on real threat intelligence and patterns seen in active breach investigations.
Forensics-led design
Simulations informed by SISA’s deep expertise in digital forensics and incident response.
Expert execution
Delivered by specialists with hands-on knowledge of red teaming, threat hunting, and compliance.
Actionable outcomes
Clear, prioritized insights on detection gaps, control effectiveness, and use case improvements.
Ready to challenge your defenses?
Let’s run the simulation – before someone else runs the real thing.
Talk to SISA to schedule your breach and attack simulation and take the next step toward stronger, smarter cybersecurity.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube








