INTERNAL FORENSIC INVESTIGATION
When a security incident occurs, uncertainty becomes the biggest risk. Internal Forensic Investigation provides a structured approach to uncover how the incident began, the extent of its reach, and its impact on the organization. The process relies on proven forensic techniques to collect evidence, reconstruct events, and provide clarity for business leaders, regulators, and legal teams.
When is an Internal Forensic Investigation required?
Internal forensic investigations are necessary when organizations face incidents that cannot be explained by routine monitoring. Common triggers include:
Email impersonation
Fraudulent emails that attempt to mislead employees or customers.
Data breaches
Exposure of sensitive customer or business information.
Unauthorized access
Intruders gaining entry to critical systems or accounts.
Malware and ransomware
Infections that disrupt operations or compromise data.
Insider activity
Suspected fraud, misconduct, or misuse of systems by employees.
From Detection to Resolution: How SISA Sappers Investigates
SISA Sappers, our specialist DFIR unit, resolves incidents with a proven forensic methodology that blends speed and precision. Every investigation is handled with business-ready clarity, regulatory alignment, and actionable outcomes.
Investigation Approach
 Scoping the incident
Scoping the incident
Once a trigger is identified, the first step is to understand the situation: which systems are affected, what indicators are present, and what business risks are involved.
 Evidence collection and triage
Evidence collection and triage
Investigators then gather digital artifacts and run preliminary checks. If a compromise is confirmed, containment measures, such as isolating systems or resetting credentials are advised immediately to limit further exposure.
 Forensic imaging
Forensic imaging
Suspected systems are imaged at the bit-level to preserve integrity. This ensures evidence can be used for in-depth analysis or legal review without being altered.
 In-depth analysis
In-depth analysis
The investigation reconstructs the full kill chain:
- Ingress point - How attackers got in.
- Lateral movement - How they navigated the network.
- Egress point - What data was accessed or extracted.
 Reporting and recommendations
Reporting and recommendations
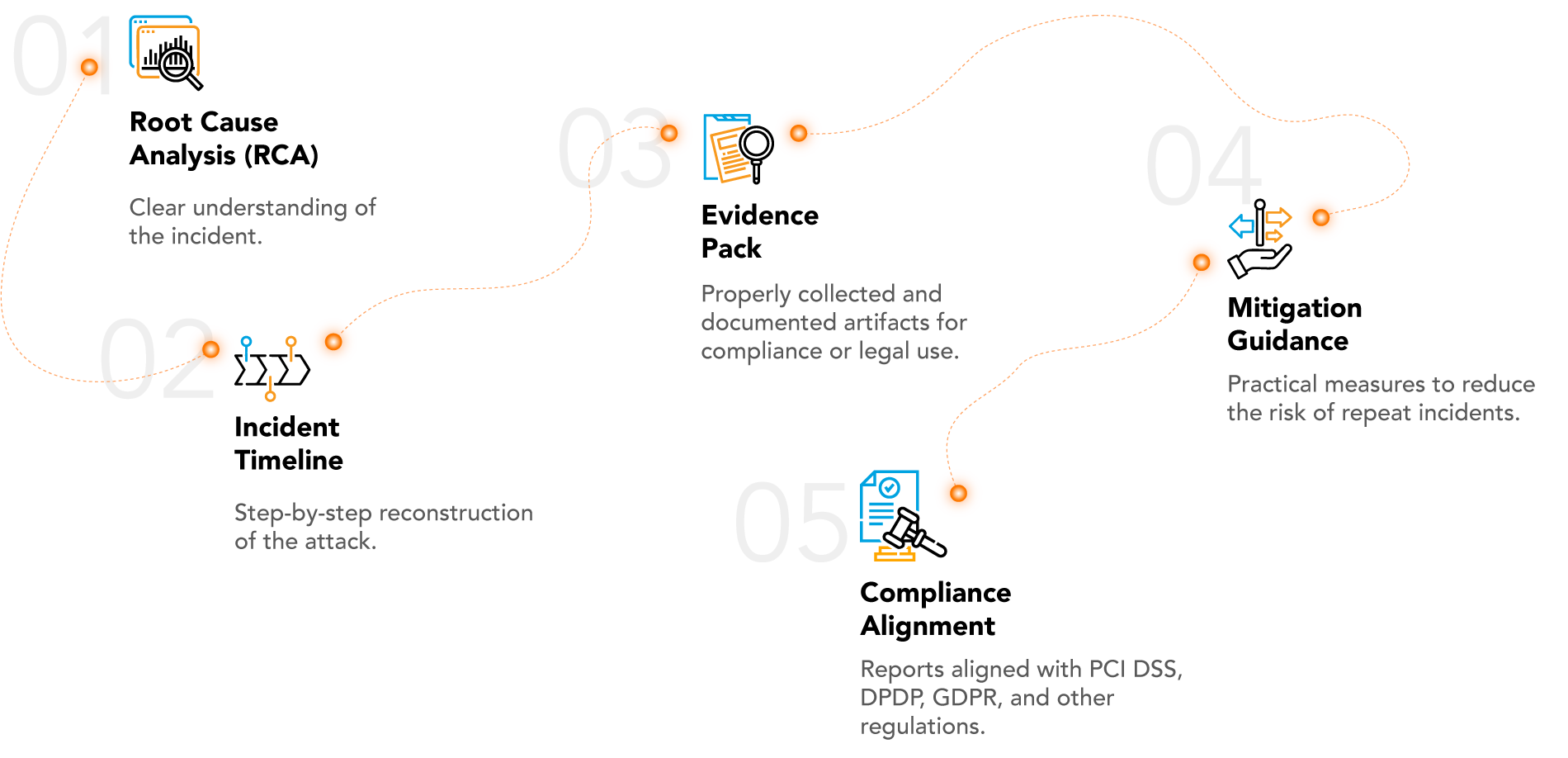
Finally, a detailed Root Cause Analysis (RCA) is presented, mapping the incident timeline, vulnerabilities exploited, and impact. In addition, practical recommendations are provided to remediate weaknesses, improve readiness, and meet compliance requirements.
Why Organizations Trust SISA and Sappers
Proven case experience
Hundreds of high-stakes investigations resolved across BFSI, fintech, and payment ecosystems worldwide.
Depth in forensics
Advanced capabilities in memory forensics, log correlation, malware reverse engineering, and endpoint analysis.
Regulatory-aligned expertise
Investigations designed to meet global compliance standards such as PCI DSS, DPDP, and GDPR.
Evidence that stands up
Strict chain-of-custody procedures and defensible reporting trusted in audits, regulatory reviews, and legal proceedings.
Faster time-to-clarity
Ability to reconstruct kill chains and deliver RCA within days, enabling quicker decision-making and response.
Industry-specific expertise
Deep familiarity with card payment systems, core banking environments, and cloud-native infrastructures.
Think you’re facing an incident?
Don’t wait for it to escalate. Contact SISA’s Sappers forensic experts today to secure
evidence, uncover facts, and safeguard your business.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube






