
Hardware and IoT Security
Testing Services
Outsmart vulnerabilities and secure your IoT ecosystem
IoT is poised for mainstream use across industries. Despite this advancement, critical questions of security remain

- How secure is communication between the device and other systems (e.g. encryption, authentication, authorization)?
- How is personal data collected, stored, and protected on the device?
- How is access to the device controlled and monitored?
- What is the incident response and disaster recovery plan, in the event of a breach?
- Are there any legal or regulatory compliance requirements related to IoT security?
Enable end-end protection of your devices with SISA's unique forensics-driven IoT Security Testing framework
A comprehensive risk-based testing approach to secure your IoT systems

Identify
Cutting-edge tools and operations to identify critical vulnerabilities by applying global industry standards and best practices.

Patch
Tailor-made recommendations to patch the discovered vulnerabilities in an optimal way.

Remediate
Ensure thorough remediation of vulnerabilities by conducting extensive retesting and review to block all loopholes.
Delivered by a dedicated team of IoT security sentinels
Reconnaissance
Collecting relevant information on the IoT ecosystem or IoT devices to identify and map potential attack vectors.
Collecting relevant information on the IoT ecosystem or IoT devices to identify and map potential attack vectors.
Modelling attacks
Leveraging threat modelling to map potential attacks against IoT ecosystem, and creating a system diagram to capture the same.
Leveraging threat modelling to map potential attacks against IoT ecosystem, and creating a system diagram to capture the same.
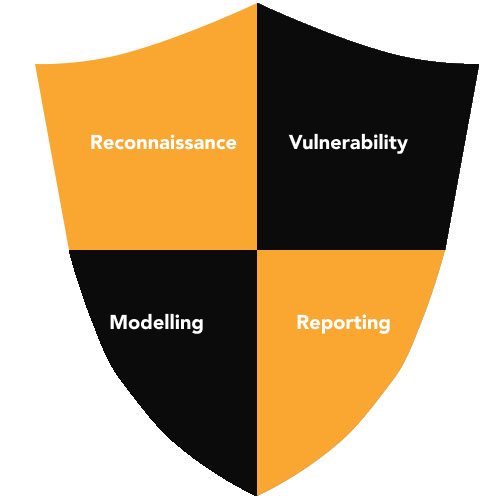
Vulnerability assessment and exploitation
Identifying and prioritizing vulnerabilities based on potential impact and manually validating the exploits against the system.
Identifying and prioritizing vulnerabilities based on potential impact and manually validating the exploits against the system.
Reporting, Remediation, and Revalidation (R3)
Identifying and prioritizing vulnerabilities based on potential impact and manually validating the exploits against the system.
Identifying and prioritizing vulnerabilities based on potential impact and manually validating the exploits against the system.

Eliminate blind spots with SISA’s IoT security testing services, tailored to meet the needs of your IoT ecosystem
Firmware security testing
- Reverse engineering
- Source code Analysis
- Dynamic analysis
- Evaluating third-party and Interconnected
- libraries
- Binary exploitation
- Identifying vulnerabilities
- Firmware Backdooring
IoT communication protocol and RF security analysis
- Traffic analysis
- Encryption and cryptographic analysis
- Evaluation of the IoT device’s crucial communication routes, ports, and services.
- Configuration evaluation
- Analysis of various communication protocols used by IoT products
- Assessment of Over-the-Air (OTA) update
- Replay and Man-in-the-middle attacks
- Analysis of distributed denial-of-service (DDoS) attacks
- Fuzzing of the communication protocols
- Security analysis of Radio frequency (RF) protocols (BLE, Zigbee, Z-wave, LoRa, etc.…) and Cellular communication (GSM, LTE, 3,4,5G)
IoT network testing
- Device discovery
- Vulnerability identification
- Penetration Testing
- Configuration risk analysis
- Lifecycle risk analysis
IoT embedded and hardware security testing
- Side channel Analysis
- Glitching Attacks
- USB Attacks
- Evaluating Debug ports for potential exploitation
- Hardware-based firmware extraction
- Assessing against malicious firmware update
- Secure boot assessment
- Hardware based sniffing and tampering
IoT hardware/embedded assessment
- Side channel Analysis
- Glitching Attacks
- USB Attacks
- Evaluating Debug ports for potential exploitation
- Hardware-based firmware extraction
- Assessing against malicious firmware update
- Secure boot assessment
- Hardware based sniffing and tampering
IoT application and management layer testing
- Functional level evaluation
- Web and Mobile application Testing
- Cloud services and API testing
- Fuzzing
- Evaluation of management and control layer for Internet of Things systems.
- Connectivity and Interoperability testing
Compliance certification for enterprises and manufacturers.
- Consultation for IoT security standards
- Consultation for ISO/IEC 27400:2022 , ISO/IEC DIS 27402
Achieve seamless functionality and improved IoT security for your intelligent products

Increase sales up to 30% by establishing customer confidence.

Address up to 70% of security issues earlier in the product lifecycle.

Reduce a product's time to market by up to 30% with our advanced testing methods.
Improve your product security posture up to 45%.

Get the forensics advantage with SISA’s IoT
security testing services
0
+
IoT Devices Tested
0
+
IoT use cases scenarios covered
0
+
Instances of sensitive IoT data secured
0
+
team of security experts
Leading brands work with us









Exclusive IoT security masterclass session
Get the latest insights IoT attacks in the Fintech Industry, adversarial TTP’s related to IoT attacks and best practices to protect your organization from IoT Ransomware, malware and breaches.
Request a Call

SISA is a global forensics-driven cybersecurity solutions company, trusted by leading organizations for securing their businesses with robust preventive, detective, and corrective cybersecurity solutions. Our problem-first, human-centric approach helps businesses strengthen their cybersecurity posture.
Industry recognition by CREST, CERT-In and PCI SSC serves as a testament to our skill, knowledge, and competence.
We apply the power of forensic intelligence and advanced technology to offer true security to 2,000+ customers in 40+ countries.
Company
Resources
Quick Links
Copyright © 2024 SISA. All Rights Reserved.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global


 Facebook
Facebook Linkedin
Linkedin  Twitter
Twitter Youtube
Youtube






